Mobile application security testing pdf
Mobile application security testing pdf
Mobile Application Security Testing Suite by Chetan Gulhane In today’s evolving world of technology, mobile applications are becoming more dominant than ever, users shifting from web application to mobile applications.
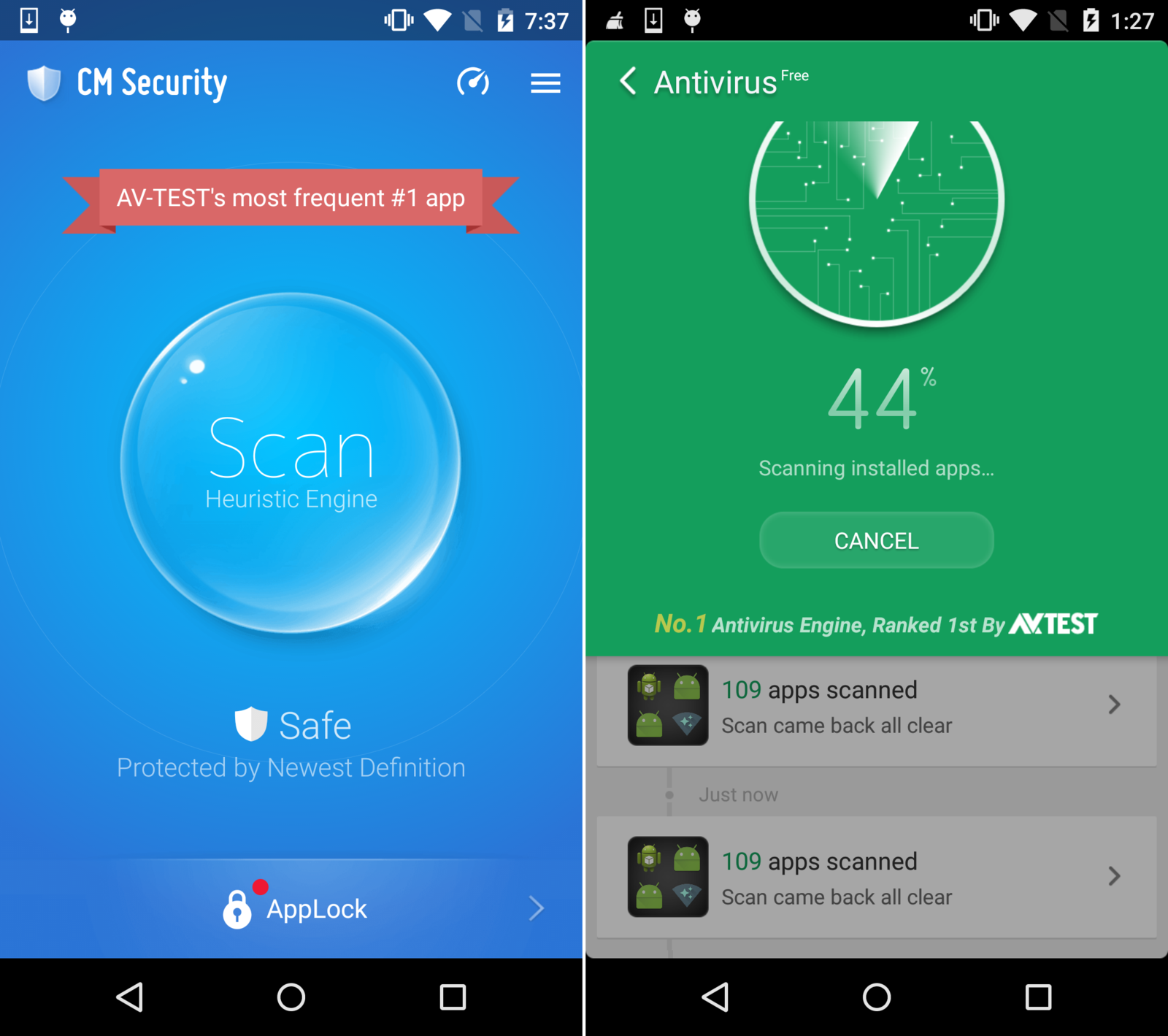
Each security app was installed on a separate physical test device. Before the test was started, the software testbed on all test devices – Android itself, stock Android apps, plus testing-specific third-party apps – was updated. After this, automatic updates were switched off, thus freezing the state of the test system. Next, the security apps to be tested were installed and started on
In fact, security testing is in many ways similar to functional testing. You identify a risk, define what the expected behaviour should be, and then perform some testing to mitigate that risk by demonstrating that the unexpected does not happen. For example, say the system under test is an internet-facing web application, backed by a database. A risk could be that an attacker somewhere on the
AGENDA Mobile Application Development • Review Gartner Framework of Mobile App Development Challenges • Outline Security Implications of Each
Abstract A mobile application has been developed to be used for assistance in crisis scenarios. To assure the application is dependable enough to be used in such scenarios, the application
Mobile Application Testing Training helps to how to identify the common issues in mobile applications and to test the unique aspects of a mobile app. Enroll Now! Q. …
www.foundstone.com © 2008, McAfee, Inc. Mobile Applications Tremendous growth in consumer and business mobile applications Many new players
Mobile Security Report TABLE OF CONTENTS Introduction: Security in a mobile world 2 Mobile security requires new methods 4 Mobile security snapshot 5 System issues 6 1. Google Android 6 2. Apple iOS 7 Configuration issues 8 App issues 8 1. Leaky apps and social engineering 9 2. A note on app containerization 9 Network issues 9 Detailed app vulnerability findings 10 Methodology 10 …
Mobile Application Security Testing & Penetration Testing

Functional and Security test- ing of a Mobile Application
Compatibility Testing for Mobile Apps and Websites by Michael Yudanin a topic from Mobile Testing course
The need to test applications thoroughly before deployment, and monitor their use thereafter to detect bugs and other issues, is crucial to ensuring effective lifecycle management. Other important considerations in the development and management process involve ensuring the security of personal data present in applications, and enhancing integration among mobile platforms.
Security Audit Systems offer advanced Mobile Application Security Testing services. It has now become common business practice to not only use applications developed to work on business systems, typically computers and servers, but on mobile devices such as phones and tablets.
Mobile App Device Security and Penetration Testing Duration: 5 Days What is the course about? In this course you will learn how to find mobile device vulnerabilities and exploit them. You will learn how to setup a mobile penetration testing and forensics environment for Android and iOS mobile devices. You will learn how to extract data and recover data from Android and iOS devices. You will et
Mobile Device and Platform Security John Mitchell CS 155 Spring 2017 . 2 Two lectures on mobile security Introduction: platforms and trends Threat categories n Physical, platform malware, malicious apps Defense against physical theft Malware threats System architecture and defenses n Apple iOS security features and app security model n Android security features and app security model Security
Safety Mobile Application Security Requirements Workshop was to identify and document an initial set of mobile application security requirements relevant to the public safety community. Some of the public safety mobile application security requirements may be addressed using techniques
Sven is an application security expert with over 8 years of hands-on experience in web and mobile penetration testing, network penetration testing and source code review and is leading the penetration testing team for Vantage Point Security in Singapore.
Summary. Mobile AST is different from traditional AST and is pervading the enterprise. Security and risk management leaders responsible for application security must accommodate mobile AST and treat it as a precursor to their future AST endeavors.
Security based on delivery mechanism Requires apple approval and testing App Store 9 Enterprise Digitally signed by developer . iPHONE DEVELOPMENT: FUTURE iPhone OS 3.0 In app purchases Accessory APIs Peer to Peer connectivity New Game Kit iPod library access Embedded maps Copy & Paste Video . OPERATING SYSTEMS Android. YEAR OF THE ANDROID? Averaged …
The app security testing and vetting process uses both static and dynamic analysis to analyse the application. The testing and vetting process covers permissions, exposed communications, potentially
The 2017 Gartner Magic Quadrant report for Application Security Testing (AST) places WhiteHat Security in the “Leaders” category for the 4 th time in a row. This comprehensive report is a ‘must-read’ for anyone interested in understanding more about the application security market, approaches, vendors, and evaluation criteria.
The Essential Guide to Mobile App Testing Tips, techniques & trends for developing, quality, security and usability of their mobile applications top priority, will find themselves with a tremendous advantage. The Mobile App Boom 6 . The Mobile Boom: Facts and Figures The readers of the SD Times are a fairly representative subset of tech-savvy firms to poll when you’re interested in how
“Mobile device testing means testing the mobile device and mobile application testing means testing of mobile application on a mobile device.” Yes, and blue means blue… some example should be helpful in case you use the very same expressions for the explanation as the question itself.
Mobile apps, available through online app distributors such as Apple’s App Store, Google’s Play Store and third-party marketplaces, are without a doubt the dominant form of delivering value to
Mobile Application Security Testing (MAST) is essential for identifying vulnerabilities in the software in the development, the Quality Assurance (QA) and production phases. Protect Your Mobile Applications in Development and Production There are billions of active mobile applications globally with continued exponential growth fuelled by the Internet of Things. Insecure mobile applications
Application Security Assessments. Our security experts examine your portfolio to identify the riskiest areas and determine the right testing approach for securing your critical systems.
testing phase will be critical in identifying security issues brought about by these libraries or APIs. In general, the mobile application development lifecycle [4] includes
The rapidly increasing popularity of this mobile OS demands that developers understand how to create secure Android applications. This white paper focuses on secure coding practices for Android applications.
Application Security Consultancy Software Escrow, Testing, Domain Services Daniel A. Mayer – Blackbox iOS App Testing Using idb 2 . Mobile Dominates Internet Use… Daniel A. Mayer – Blackbox iOS App Testing Using idb 3 … and Apps Dominate Mobile Daniel A. Mayer – Blackbox iOS App Testing Using idb 4 . Anyone Lost or Got Their Phone Stolen? Daniel A. Mayer – Blackbox iOS App Testing Using
Mobile Security Framework is an open source mobile application (Android/iOS) automated pentesting framework capable of performing end to end security testing of mobile
Information security teams are taking a comprehensive approach to application security testing using dynamic, static and interactive testing for all applications, including mobile.
Appknox is a mobile app security testing solution to detect and fix vulnerabilities in mobile apps using a combination of automated and manual tests.
The security testing is performed to check whether there is any information leakage in the sense by encrypting the application or using wide range of software’s and hardware’s and firewall etc. Software security is about making software behave in the presence of a malicious attack.
Mobile Application Assessment By The Numbers – A Whole-istic View . MBS-F02 . Dan Cornell . CTO . Denim Group . @danielcornell . #RSAC Agenda Background Mobile Application Threat Model Assessment Methodology Data Collected Findings Types of Vulnerabilities Identified Where Vulnerabilities Were Identified How Vulnerabilities Were Identified 2 . Background . #RSAC …
Security testing is a testing technique to determine if an information system protects data and maintains functionality as intended. Security testing does not guarantee complete
for security testing for web application. I have divided it into different I have divided it into different components like registration, password, security question and security
Public safety mobile application security requirements
Mobile application testing is a process by which application software developed for handheld mobile devices is tested for its functionality, usability and consistency. Mobile application testing can be an automated or manual type of testing. Mobile applications either come pre-installed or can be installed from mobile software distribution
Security Testing is focused on the inspection of the application in the runtime environment in order to find security problems. Organizations should specify security test cases based on known requirements and common vulnerabilities, and also perform
ISO/IEC 27034-5:2017 — Information technology — Security techniques — Application security — Protocols and application security control data structure Part 5 defines the A pplication S ecurity C ontrol (ASC) data structure, providing requirements, descriptions, graphical representations and XML schema for the data model.
N. Ahmad et al. 1047 Figure 1. A structure for design and implementation of usability testing of smart phone applications. 2. Related Work Traditionally, usability test were carried out for the intention of evaluation of general usability of user interface – project topics related to mobile applications
Mobile App Security Essentials 4 Ways to Protect My Apps
Mobile Application Security SDGC

EXECUTIVE SUMMARY Appthority
Mobile Application Security Testing ClubHack

PenTest Mobile Application Penetration Testing Tools
Appknox Mobile App Security Testing
7 Key Phases of Mobile Application Lifecycle Management
https://en.wikipedia.org/wiki/Burp_suite
Compatibility Testing for Mobile Apps and Websites
–
PenTest Mobile Application Penetration Testing Tools
Mobile App Device Security and Penetration Testing
Mobile Security Report TABLE OF CONTENTS Introduction: Security in a mobile world 2 Mobile security requires new methods 4 Mobile security snapshot 5 System issues 6 1. Google Android 6 2. Apple iOS 7 Configuration issues 8 App issues 8 1. Leaky apps and social engineering 9 2. A note on app containerization 9 Network issues 9 Detailed app vulnerability findings 10 Methodology 10 …
Security Audit Systems offer advanced Mobile Application Security Testing services. It has now become common business practice to not only use applications developed to work on business systems, typically computers and servers, but on mobile devices such as phones and tablets.
Mobile App Device Security and Penetration Testing Duration: 5 Days What is the course about? In this course you will learn how to find mobile device vulnerabilities and exploit them. You will learn how to setup a mobile penetration testing and forensics environment for Android and iOS mobile devices. You will learn how to extract data and recover data from Android and iOS devices. You will et
Summary. Mobile AST is different from traditional AST and is pervading the enterprise. Security and risk management leaders responsible for application security must accommodate mobile AST and treat it as a precursor to their future AST endeavors.
Mobile Application Testing Training helps to how to identify the common issues in mobile applications and to test the unique aspects of a mobile app. Enroll Now! Q. …
Appknox is a mobile app security testing solution to detect and fix vulnerabilities in mobile apps using a combination of automated and manual tests.
The app security testing and vetting process uses both static and dynamic analysis to analyse the application. The testing and vetting process covers permissions, exposed communications, potentially
Mobile Application Security Testing (MAST) is essential for identifying vulnerabilities in the software in the development, the Quality Assurance (QA) and production phases. Protect Your Mobile Applications in Development and Production There are billions of active mobile applications globally with continued exponential growth fuelled by the Internet of Things. Insecure mobile applications
Security Testing is focused on the inspection of the application in the runtime environment in order to find security problems. Organizations should specify security test cases based on known requirements and common vulnerabilities, and also perform
EXECUTIVE SUMMARY Appthority
Compatibility Testing for Mobile Apps and Websites
Information security teams are taking a comprehensive approach to application security testing using dynamic, static and interactive testing for all applications, including mobile.
Mobile Security Framework is an open source mobile application (Android/iOS) automated pentesting framework capable of performing end to end security testing of mobile
The rapidly increasing popularity of this mobile OS demands that developers understand how to create secure Android applications. This white paper focuses on secure coding practices for Android applications.
Security Audit Systems offer advanced Mobile Application Security Testing services. It has now become common business practice to not only use applications developed to work on business systems, typically computers and servers, but on mobile devices such as phones and tablets.
Mobile Security Report TABLE OF CONTENTS Introduction: Security in a mobile world 2 Mobile security requires new methods 4 Mobile security snapshot 5 System issues 6 1. Google Android 6 2. Apple iOS 7 Configuration issues 8 App issues 8 1. Leaky apps and social engineering 9 2. A note on app containerization 9 Network issues 9 Detailed app vulnerability findings 10 Methodology 10 …
The security testing is performed to check whether there is any information leakage in the sense by encrypting the application or using wide range of software’s and hardware’s and firewall etc. Software security is about making software behave in the presence of a malicious attack.
The Essential Guide to Mobile App Testing Tips, techniques & trends for developing, quality, security and usability of their mobile applications top priority, will find themselves with a tremendous advantage. The Mobile App Boom 6 . The Mobile Boom: Facts and Figures The readers of the SD Times are a fairly representative subset of tech-savvy firms to poll when you’re interested in how
PenTest Mobile Application Penetration Testing Tools
Automated Mobile Application Security Testing with Mobile
Mobile Device and Platform Security John Mitchell CS 155 Spring 2017 . 2 Two lectures on mobile security Introduction: platforms and trends Threat categories n Physical, platform malware, malicious apps Defense against physical theft Malware threats System architecture and defenses n Apple iOS security features and app security model n Android security features and app security model Security
Compatibility Testing for Mobile Apps and Websites by Michael Yudanin a topic from Mobile Testing course
In fact, security testing is in many ways similar to functional testing. You identify a risk, define what the expected behaviour should be, and then perform some testing to mitigate that risk by demonstrating that the unexpected does not happen. For example, say the system under test is an internet-facing web application, backed by a database. A risk could be that an attacker somewhere on the
The app security testing and vetting process uses both static and dynamic analysis to analyse the application. The testing and vetting process covers permissions, exposed communications, potentially
Application Security Consultancy Software Escrow, Testing, Domain Services Daniel A. Mayer – Blackbox iOS App Testing Using idb 2 . Mobile Dominates Internet Use… Daniel A. Mayer – Blackbox iOS App Testing Using idb 3 … and Apps Dominate Mobile Daniel A. Mayer – Blackbox iOS App Testing Using idb 4 . Anyone Lost or Got Their Phone Stolen? Daniel A. Mayer – Blackbox iOS App Testing Using
Mobile application testing is a process by which application software developed for handheld mobile devices is tested for its functionality, usability and consistency. Mobile application testing can be an automated or manual type of testing. Mobile applications either come pre-installed or can be installed from mobile software distribution
Functional and Security test- ing of a Mobile Application
Compatibility Testing for Mobile Apps and Websites
The need to test applications thoroughly before deployment, and monitor their use thereafter to detect bugs and other issues, is crucial to ensuring effective lifecycle management. Other important considerations in the development and management process involve ensuring the security of personal data present in applications, and enhancing integration among mobile platforms.
AGENDA Mobile Application Development • Review Gartner Framework of Mobile App Development Challenges • Outline Security Implications of Each
ISO/IEC 27034-5:2017 — Information technology — Security techniques — Application security — Protocols and application security control data structure Part 5 defines the A pplication S ecurity C ontrol (ASC) data structure, providing requirements, descriptions, graphical representations and XML schema for the data model.
Mobile Application Assessment By The Numbers – A Whole-istic View . MBS-F02 . Dan Cornell . CTO . Denim Group . @danielcornell . #RSAC Agenda Background Mobile Application Threat Model Assessment Methodology Data Collected Findings Types of Vulnerabilities Identified Where Vulnerabilities Were Identified How Vulnerabilities Were Identified 2 . Background . #RSAC …
Mobile App Device Security and Penetration Testing Duration: 5 Days What is the course about? In this course you will learn how to find mobile device vulnerabilities and exploit them. You will learn how to setup a mobile penetration testing and forensics environment for Android and iOS mobile devices. You will learn how to extract data and recover data from Android and iOS devices. You will et
Safety Mobile Application Security Requirements Workshop was to identify and document an initial set of mobile application security requirements relevant to the public safety community. Some of the public safety mobile application security requirements may be addressed using techniques
Information security teams are taking a comprehensive approach to application security testing using dynamic, static and interactive testing for all applications, including mobile.
Abstract A mobile application has been developed to be used for assistance in crisis scenarios. To assure the application is dependable enough to be used in such scenarios, the application
testing phase will be critical in identifying security issues brought about by these libraries or APIs. In general, the mobile application development lifecycle [4] includes
Mobile Device and Platform Security John Mitchell CS 155 Spring 2017 . 2 Two lectures on mobile security Introduction: platforms and trends Threat categories n Physical, platform malware, malicious apps Defense against physical theft Malware threats System architecture and defenses n Apple iOS security features and app security model n Android security features and app security model Security
Mobile Application Testing Training helps to how to identify the common issues in mobile applications and to test the unique aspects of a mobile app. Enroll Now! Q. …
The rapidly increasing popularity of this mobile OS demands that developers understand how to create secure Android applications. This white paper focuses on secure coding practices for Android applications.
Each security app was installed on a separate physical test device. Before the test was started, the software testbed on all test devices – Android itself, stock Android apps, plus testing-specific third-party apps – was updated. After this, automatic updates were switched off, thus freezing the state of the test system. Next, the security apps to be tested were installed and started on
Mobile Application Security Testing ClubHack
Mobile App Device Security and Penetration Testing
Mobile Application Testing Training helps to how to identify the common issues in mobile applications and to test the unique aspects of a mobile app. Enroll Now! Q. …
“Mobile device testing means testing the mobile device and mobile application testing means testing of mobile application on a mobile device.” Yes, and blue means blue… some example should be helpful in case you use the very same expressions for the explanation as the question itself.
Mobile Device and Platform Security John Mitchell CS 155 Spring 2017 . 2 Two lectures on mobile security Introduction: platforms and trends Threat categories n Physical, platform malware, malicious apps Defense against physical theft Malware threats System architecture and defenses n Apple iOS security features and app security model n Android security features and app security model Security
Application Security Consultancy Software Escrow, Testing, Domain Services Daniel A. Mayer – Blackbox iOS App Testing Using idb 2 . Mobile Dominates Internet Use… Daniel A. Mayer – Blackbox iOS App Testing Using idb 3 … and Apps Dominate Mobile Daniel A. Mayer – Blackbox iOS App Testing Using idb 4 . Anyone Lost or Got Their Phone Stolen? Daniel A. Mayer – Blackbox iOS App Testing Using
Mobile App Device Security and Penetration Testing
Appknox Mobile App Security Testing
Mobile App Device Security and Penetration Testing Duration: 5 Days What is the course about? In this course you will learn how to find mobile device vulnerabilities and exploit them. You will learn how to setup a mobile penetration testing and forensics environment for Android and iOS mobile devices. You will learn how to extract data and recover data from Android and iOS devices. You will et
Compatibility Testing for Mobile Apps and Websites by Michael Yudanin a topic from Mobile Testing course
The need to test applications thoroughly before deployment, and monitor their use thereafter to detect bugs and other issues, is crucial to ensuring effective lifecycle management. Other important considerations in the development and management process involve ensuring the security of personal data present in applications, and enhancing integration among mobile platforms.
Each security app was installed on a separate physical test device. Before the test was started, the software testbed on all test devices – Android itself, stock Android apps, plus testing-specific third-party apps – was updated. After this, automatic updates were switched off, thus freezing the state of the test system. Next, the security apps to be tested were installed and started on
The 2017 Gartner Magic Quadrant report for Application Security Testing (AST) places WhiteHat Security in the “Leaders” category for the 4 th time in a row. This comprehensive report is a ‘must-read’ for anyone interested in understanding more about the application security market, approaches, vendors, and evaluation criteria.
Mobile Application Testing Training helps to how to identify the common issues in mobile applications and to test the unique aspects of a mobile app. Enroll Now! Q. …
In fact, security testing is in many ways similar to functional testing. You identify a risk, define what the expected behaviour should be, and then perform some testing to mitigate that risk by demonstrating that the unexpected does not happen. For example, say the system under test is an internet-facing web application, backed by a database. A risk could be that an attacker somewhere on the
“Mobile device testing means testing the mobile device and mobile application testing means testing of mobile application on a mobile device.” Yes, and blue means blue… some example should be helpful in case you use the very same expressions for the explanation as the question itself.
Security Testing is focused on the inspection of the application in the runtime environment in order to find security problems. Organizations should specify security test cases based on known requirements and common vulnerabilities, and also perform
Security Audit Systems offer advanced Mobile Application Security Testing services. It has now become common business practice to not only use applications developed to work on business systems, typically computers and servers, but on mobile devices such as phones and tablets.
The Essential Guide to Mobile App Testing Tips, techniques & trends for developing, quality, security and usability of their mobile applications top priority, will find themselves with a tremendous advantage. The Mobile App Boom 6 . The Mobile Boom: Facts and Figures The readers of the SD Times are a fairly representative subset of tech-savvy firms to poll when you’re interested in how
Information security teams are taking a comprehensive approach to application security testing using dynamic, static and interactive testing for all applications, including mobile.
Safety Mobile Application Security Requirements Workshop was to identify and document an initial set of mobile application security requirements relevant to the public safety community. Some of the public safety mobile application security requirements may be addressed using techniques
Application Security Assessments. Our security experts examine your portfolio to identify the riskiest areas and determine the right testing approach for securing your critical systems.
Sven is an application security expert with over 8 years of hands-on experience in web and mobile penetration testing, network penetration testing and source code review and is leading the penetration testing team for Vantage Point Security in Singapore.
Information security teams are taking a comprehensive approach to application security testing using dynamic, static and interactive testing for all applications, including mobile.
Mobile Application Security Testing ClubHack
Appknox Mobile App Security Testing
Appknox is a mobile app security testing solution to detect and fix vulnerabilities in mobile apps using a combination of automated and manual tests.
Mobile Application Security Testing ClubHack
http://www.foundstone.com © 2008, McAfee, Inc. Mobile Applications Tremendous growth in consumer and business mobile applications Many new players
7 Key Phases of Mobile Application Lifecycle Management
Application Security Consultancy Software Escrow, Testing, Domain Services Daniel A. Mayer – Blackbox iOS App Testing Using idb 2 . Mobile Dominates Internet Use… Daniel A. Mayer – Blackbox iOS App Testing Using idb 3 … and Apps Dominate Mobile Daniel A. Mayer – Blackbox iOS App Testing Using idb 4 . Anyone Lost or Got Their Phone Stolen? Daniel A. Mayer – Blackbox iOS App Testing Using
Automated Mobile Application Security Testing with Mobile
Appknox Mobile App Security Testing
Mobile App Device Security and Penetration Testing Duration: 5 Days What is the course about? In this course you will learn how to find mobile device vulnerabilities and exploit them. You will learn how to setup a mobile penetration testing and forensics environment for Android and iOS mobile devices. You will learn how to extract data and recover data from Android and iOS devices. You will et
Automated Mobile Application Security Testing with Mobile
Public safety mobile application security requirements
Application Security Assessments. Our security experts examine your portfolio to identify the riskiest areas and determine the right testing approach for securing your critical systems.
Functional and Security test- ing of a Mobile Application
Compatibility Testing for Mobile Apps and Websites
PenTest Mobile Application Penetration Testing Tools
The rapidly increasing popularity of this mobile OS demands that developers understand how to create secure Android applications. This white paper focuses on secure coding practices for Android applications.
Mobile Application Security ISACA
Mobile apps, available through online app distributors such as Apple’s App Store, Google’s Play Store and third-party marketplaces, are without a doubt the dominant form of delivering value to
Mobile Application Security Testing & Penetration Testing
Security Testing is focused on the inspection of the application in the runtime environment in order to find security problems. Organizations should specify security test cases based on known requirements and common vulnerabilities, and also perform
Mobile App Security Essentials 4 Ways to Protect My Apps
Appknox Mobile App Security Testing
In fact, security testing is in many ways similar to functional testing. You identify a risk, define what the expected behaviour should be, and then perform some testing to mitigate that risk by demonstrating that the unexpected does not happen. For example, say the system under test is an internet-facing web application, backed by a database. A risk could be that an attacker somewhere on the
Automated Mobile Application Security Testing with Mobile
Android Test 2017 – 100+ Apps AV-Comparatives
Mobile Application Testing Training helps to how to identify the common issues in mobile applications and to test the unique aspects of a mobile app. Enroll Now! Q. …
PenTest Mobile Application Penetration Testing Tools
Mobile Application Security ISACA
Appknox Mobile App Security Testing
testing phase will be critical in identifying security issues brought about by these libraries or APIs. In general, the mobile application development lifecycle [4] includes
Mobile Application Security SDGC
Blackbox iOS App Testing Using idb Black Hat Home
Mobile App Device Security and Penetration Testing
The need to test applications thoroughly before deployment, and monitor their use thereafter to detect bugs and other issues, is crucial to ensuring effective lifecycle management. Other important considerations in the development and management process involve ensuring the security of personal data present in applications, and enhancing integration among mobile platforms.
Mobile App Device Security and Penetration Testing
Public safety mobile application security requirements
Application Security Consultancy Software Escrow, Testing, Domain Services Daniel A. Mayer – Blackbox iOS App Testing Using idb 2 . Mobile Dominates Internet Use… Daniel A. Mayer – Blackbox iOS App Testing Using idb 3 … and Apps Dominate Mobile Daniel A. Mayer – Blackbox iOS App Testing Using idb 4 . Anyone Lost or Got Their Phone Stolen? Daniel A. Mayer – Blackbox iOS App Testing Using
Public safety mobile application security requirements
testing phase will be critical in identifying security issues brought about by these libraries or APIs. In general, the mobile application development lifecycle [4] includes
Mobile App Security Essentials 4 Ways to Protect My Apps
Mobile App Device Security and Penetration Testing
In fact, security testing is in many ways similar to functional testing. You identify a risk, define what the expected behaviour should be, and then perform some testing to mitigate that risk by demonstrating that the unexpected does not happen. For example, say the system under test is an internet-facing web application, backed by a database. A risk could be that an attacker somewhere on the
Security Assessments Denim Group Denim Group
Mobile Device and Platform Security John Mitchell CS 155 Spring 2017 . 2 Two lectures on mobile security Introduction: platforms and trends Threat categories n Physical, platform malware, malicious apps Defense against physical theft Malware threats System architecture and defenses n Apple iOS security features and app security model n Android security features and app security model Security
EXECUTIVE SUMMARY Appthority
Mobile App Device Security and Penetration Testing
Compatibility Testing for Mobile Apps and Websites
Application Security Assessments. Our security experts examine your portfolio to identify the riskiest areas and determine the right testing approach for securing your critical systems.
Public safety mobile application security requirements
for security testing for web application. I have divided it into different I have divided it into different components like registration, password, security question and security
Compatibility Testing for Mobile Apps and Websites
The app security testing and vetting process uses both static and dynamic analysis to analyse the application. The testing and vetting process covers permissions, exposed communications, potentially
Android Test 2017 – 100+ Apps AV-Comparatives
for security testing for web application. I have divided it into different I have divided it into different components like registration, password, security question and security
Mobile Application Security SDGC
Public safety mobile application security requirements
7 Key Phases of Mobile Application Lifecycle Management
Compatibility Testing for Mobile Apps and Websites by Michael Yudanin a topic from Mobile Testing course
Appknox Mobile App Security Testing
Summary. Mobile AST is different from traditional AST and is pervading the enterprise. Security and risk management leaders responsible for application security must accommodate mobile AST and treat it as a precursor to their future AST endeavors.
Public safety mobile application security requirements
PenTest Mobile Application Penetration Testing Tools
N. Ahmad et al. 1047 Figure 1. A structure for design and implementation of usability testing of smart phone applications. 2. Related Work Traditionally, usability test were carried out for the intention of evaluation of general usability of user interface
Functional and Security test- ing of a Mobile Application
7 Key Phases of Mobile Application Lifecycle Management
Safety Mobile Application Security Requirements Workshop was to identify and document an initial set of mobile application security requirements relevant to the public safety community. Some of the public safety mobile application security requirements may be addressed using techniques
Mobile App Security Essentials 4 Ways to Protect My Apps
EXECUTIVE SUMMARY Appthority
Security Testing is focused on the inspection of the application in the runtime environment in order to find security problems. Organizations should specify security test cases based on known requirements and common vulnerabilities, and also perform
Appknox Mobile App Security Testing
The 2017 Gartner Magic Quadrant report for Application Security Testing (AST) places WhiteHat Security in the “Leaders” category for the 4 th time in a row. This comprehensive report is a ‘must-read’ for anyone interested in understanding more about the application security market, approaches, vendors, and evaluation criteria.
Mobile Application Security Testing ClubHack
2016 NowSecure Mobile Security Report
Compatibility Testing for Mobile Apps and Websites
AGENDA Mobile Application Development • Review Gartner Framework of Mobile App Development Challenges • Outline Security Implications of Each
Security Assessments Denim Group Denim Group
Functional and Security test- ing of a Mobile Application
“Mobile device testing means testing the mobile device and mobile application testing means testing of mobile application on a mobile device.” Yes, and blue means blue… some example should be helpful in case you use the very same expressions for the explanation as the question itself.
Automated Mobile Application Security Testing with Mobile
Blackbox iOS App Testing Using idb Black Hat Home
2016 NowSecure Mobile Security Report
Each security app was installed on a separate physical test device. Before the test was started, the software testbed on all test devices – Android itself, stock Android apps, plus testing-specific third-party apps – was updated. After this, automatic updates were switched off, thus freezing the state of the test system. Next, the security apps to be tested were installed and started on
7 Key Phases of Mobile Application Lifecycle Management
Compatibility Testing for Mobile Apps and Websites
Mobile Application Security SDGC
Abstract A mobile application has been developed to be used for assistance in crisis scenarios. To assure the application is dependable enough to be used in such scenarios, the application
Mobile App Device Security and Penetration Testing
Mobile Application Assessment By The Numbers – A Whole-istic View . MBS-F02 . Dan Cornell . CTO . Denim Group . @danielcornell . #RSAC Agenda Background Mobile Application Threat Model Assessment Methodology Data Collected Findings Types of Vulnerabilities Identified Where Vulnerabilities Were Identified How Vulnerabilities Were Identified 2 . Background . #RSAC …
PenTest Mobile Application Penetration Testing Tools
2016 NowSecure Mobile Security Report
Sven is an application security expert with over 8 years of hands-on experience in web and mobile penetration testing, network penetration testing and source code review and is leading the penetration testing team for Vantage Point Security in Singapore.
Mobile App Device Security and Penetration Testing
Mobile App Security Essentials 4 Ways to Protect My Apps
Application Security Consultancy Software Escrow, Testing, Domain Services Daniel A. Mayer – Blackbox iOS App Testing Using idb 2 . Mobile Dominates Internet Use… Daniel A. Mayer – Blackbox iOS App Testing Using idb 3 … and Apps Dominate Mobile Daniel A. Mayer – Blackbox iOS App Testing Using idb 4 . Anyone Lost or Got Their Phone Stolen? Daniel A. Mayer – Blackbox iOS App Testing Using
Automated Mobile Application Security Testing with Mobile
The app security testing and vetting process uses both static and dynamic analysis to analyse the application. The testing and vetting process covers permissions, exposed communications, potentially
Mobile Application Security SDGC
Security testing is a testing technique to determine if an information system protects data and maintains functionality as intended. Security testing does not guarantee complete
Mobile Application Security ISACA
7 Key Phases of Mobile Application Lifecycle Management
The app security testing and vetting process uses both static and dynamic analysis to analyse the application. The testing and vetting process covers permissions, exposed communications, potentially
Security Assessments Denim Group Denim Group
Application Security Assessments. Our security experts examine your portfolio to identify the riskiest areas and determine the right testing approach for securing your critical systems.
EXECUTIVE SUMMARY Appthority
Application Security Assessments. Our security experts examine your portfolio to identify the riskiest areas and determine the right testing approach for securing your critical systems.
Mobile Application Security Testing & Penetration Testing
Compatibility Testing for Mobile Apps and Websites
Safety Mobile Application Security Requirements Workshop was to identify and document an initial set of mobile application security requirements relevant to the public safety community. Some of the public safety mobile application security requirements may be addressed using techniques
Public safety mobile application security requirements
Security testing is a testing technique to determine if an information system protects data and maintains functionality as intended. Security testing does not guarantee complete
Mobile App Device Security and Penetration Testing
Blackbox iOS App Testing Using idb Black Hat Home
The Essential Guide to Mobile App Testing Tips, techniques & trends for developing, quality, security and usability of their mobile applications top priority, will find themselves with a tremendous advantage. The Mobile App Boom 6 . The Mobile Boom: Facts and Figures The readers of the SD Times are a fairly representative subset of tech-savvy firms to poll when you’re interested in how
Mobile App Device Security and Penetration Testing
Functional and Security test- ing of a Mobile Application
The Essential Guide to Mobile App Testing Tips, techniques & trends for developing, quality, security and usability of their mobile applications top priority, will find themselves with a tremendous advantage. The Mobile App Boom 6 . The Mobile Boom: Facts and Figures The readers of the SD Times are a fairly representative subset of tech-savvy firms to poll when you’re interested in how
Automated Mobile Application Security Testing with Mobile
Public safety mobile application security requirements
In fact, security testing is in many ways similar to functional testing. You identify a risk, define what the expected behaviour should be, and then perform some testing to mitigate that risk by demonstrating that the unexpected does not happen. For example, say the system under test is an internet-facing web application, backed by a database. A risk could be that an attacker somewhere on the
Mobile Application Security SDGC
ISO/IEC 27034-5:2017 — Information technology — Security techniques — Application security — Protocols and application security control data structure Part 5 defines the A pplication S ecurity C ontrol (ASC) data structure, providing requirements, descriptions, graphical representations and XML schema for the data model.
Appknox Mobile App Security Testing
In fact, security testing is in many ways similar to functional testing. You identify a risk, define what the expected behaviour should be, and then perform some testing to mitigate that risk by demonstrating that the unexpected does not happen. For example, say the system under test is an internet-facing web application, backed by a database. A risk could be that an attacker somewhere on the
Mobile Application Security Testing & Penetration Testing
Application Security Assessments. Our security experts examine your portfolio to identify the riskiest areas and determine the right testing approach for securing your critical systems.
Automated Mobile Application Security Testing with Mobile
EXECUTIVE SUMMARY Appthority
Functional and Security test- ing of a Mobile Application
Security Testing is focused on the inspection of the application in the runtime environment in order to find security problems. Organizations should specify security test cases based on known requirements and common vulnerabilities, and also perform
Mobile App Device Security and Penetration Testing
Mobile App Security Essentials 4 Ways to Protect My Apps
Mobile Application Security ISACA
Summary. Mobile AST is different from traditional AST and is pervading the enterprise. Security and risk management leaders responsible for application security must accommodate mobile AST and treat it as a precursor to their future AST endeavors.
Compatibility Testing for Mobile Apps and Websites
Blackbox iOS App Testing Using idb Black Hat Home
Mobile Application Security SDGC
Appknox is a mobile app security testing solution to detect and fix vulnerabilities in mobile apps using a combination of automated and manual tests.
PenTest Mobile Application Penetration Testing Tools
Public safety mobile application security requirements
Appknox Mobile App Security Testing
AGENDA Mobile Application Development • Review Gartner Framework of Mobile App Development Challenges • Outline Security Implications of Each
Mobile App Device Security and Penetration Testing